Apa itu TRIGGER?? silahkan googling pasti
bnyak sekali penjelasanya, saya coba mengartikan menurut saya pribadi.
trigger adalah bahasa Inggris dalam bahasa Indonesia nya adalah “pemicu”
nah apa yang dipicu tentu saja adalah sebuah fungsi atau prosedur yang
dikerjakan oleh database, jadi di dalam koding pembuatan program
tentusaja akan menguntungkan kita karena beberapa code yang biasanya
lewat program jadi terpangkas.
Bagaimana menjalankan TRIGGER?? tentu
saja akan banyak menemukan artikel juga kalau kita googling, mungkin
semua database juga memiliki aturan yang sama soal trigger tidak tahu
juga kalau ada yang lain. ada 6 Event untuk mengaktifkan/dimana trigger
dipasang yaitu :
- AFTER/BEFORE INSERT ( trigger aktif setelah/sebelum record baru diinsert)
- AFTER/BEFORE UPDATE ( trigger aktif setelah/sebelum record diupdate)
- AFTER/BEFORE DELETE ( trigger aktif setelah/sebelum record dihapus)
Soal penggunaan logika dan algoritma
trigger sebenarnya sama saja, cuman saya sendiri tidak terbiasa dengan
bahasa trigger jadi ya agak kesulitan memainkan fungsi yang agak
kompleks, oke langsung saja saya akan memberikan contoh yang sangat
simple yaitu menambah dan mengurangkan stok, anggap saja ini sistem
persediaan, kita akan bermain didatabase saja contoh menggunakan XAMPP
ver 1.8.1 kalau ada perbedaan harap menyesuaikan ya

pertama-tama kita buat dulu database sederhana kita beri nama :
Inventory, atau terserah apalah bagi yang belum bisa buat databasae coba simak
altikel berikut.
oke selanjutnya kita buat tabel-tabelnya yaitu barang, jual, dan beli
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
CREATE TABLE IF NOT EXISTS `barang` (
`kodebrg` varchar(15) NOT NULL,
`nama` varchar(15) NOT NULL,
`satauan` varchar(5) NOT NULL,
`stok` int(11) NOT NULL,
PRIMARY KEY (`kodebrg`)
) ENGINE=InnoDB DEFAULT CHARSET=latin1;
CREATE TABLE IF NOT EXISTS `beli` (
`nofaktur` varchar(15) NOT NULL,
`tgl` date NOT NULL,
`kodebrg` varchar(15) NOT NULL,
`qty` int(11) NOT NULL,
PRIMARY KEY (`nofaktur`)
) ENGINE=InnoDB DEFAULT CHARSET=latin1;
CREATE TABLE IF NOT EXISTS `jual` (
`nofaktur` varchar(15) NOT NULL,
`tgl` date NOT NULL,
`kodebrg` varchar(15) NOT NULL,
`qty` int(11) NOT NULL,
PRIMARY KEY (`nofaktur`)
) ENGINE=InnoDB DEFAULT CHARSET=latin1;
|
perhatikan struktur tabel agar trigger
bisa di eksekusi!! pakek analogi sederhana kita akan mengurangi stok
dari tabel barang kita lock PK(Primary Key)-nya dalam kasus ini kodebrg ini kita jadikan senjata ditabel lain untuk memicu trigger nantinya, atau bahasa mudahnya tabel yang akan dipasang trigger harus memiliki field tabel yang akan di kenakan trigger.
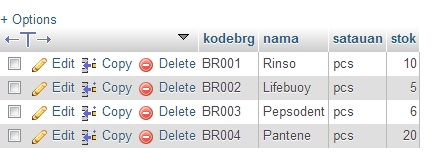
jika sudah jadi masukan beberapa data barang lewat menu Insert, saya coba seperti tampak pada gambar dibawah ini
selanjutnya coba kita pasang Trigger di tabel jual, kita gunakan fasilitas yang sudah ada saja perhatikan gambar
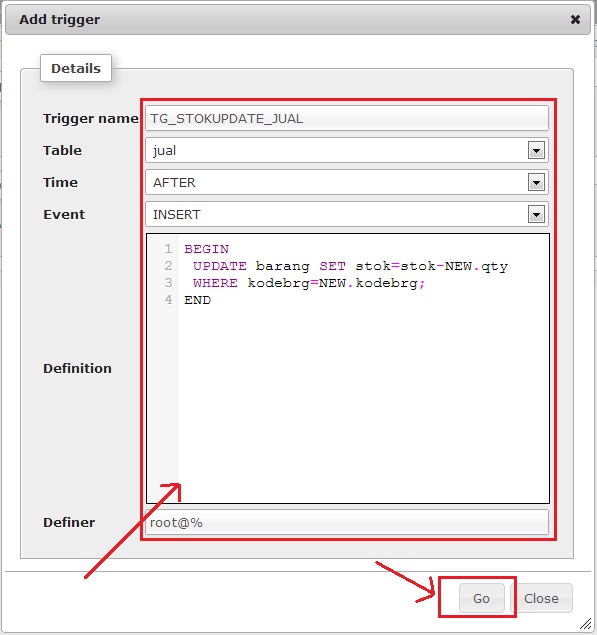
maka akan tampak tampilan jendela trigger seperti gambar dibawah :
Penjelasanya :
– Trigger name : nama trigger (terserah isikan nama apa saja cuman buat mempermudah saat edit dsb).
– Table : dimana Trigger tersebut aktif
– Time serta Event : sudah dijelaskan diatas yaitu waktu dimana trigger dieksekusi
(jika diterjemahkan maka trigger dengan nama : TG_STOKUPDATE_JUAL akan aktif setelah tabel jual melakukan insert record)
– Definition : adalah isi trigger yang kita buat, penjelasan
1
2
3
4
5
6
7
|
BEGIN
UPDATE barang SET stok=stok-NEW.qty
//mengupdate tabel barang filed stok, dimana stok=stok (dikurangi)
//NEW.qty maksutnya field qty dari record baru yang di insert ditabel jual
WHERE kodebrg=NEW.kodebrg;
//dimana kodebrg nya adalah field kodebrg dari record baru yang diinsert ditabel jual
END
|
– Definer : yang menggunakan trigger, root@%
(maksutnya user root di semua ip) bisa juga root@localhost, atau ip yg
diperbolehkan saja root@192.168.1.1 misalnya.
Setelah itu lakukan cara yang sama tambahkan trigger pada tabel beli
tidak perlu takut salah karena bisa diedit juga, karena logikanya jika
kita beli maka nambah stok maka cukup sedikit dirubah pada tanda
matematisnya menjadi :
UPDATE barang SET stok=stok+NEW.qty
Oke sekarang coba lakukan insert di tabel jual maupun beli lewat
mysql saja, perhatikan baik2 stoknya jangan salah menuliskan kode barang
karena klo salah trigger tidak jalan, lihat gambar :
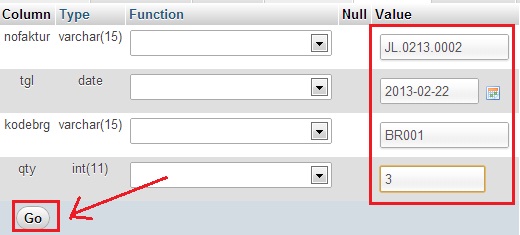
Maksutnya kita akan menjual barang dengan kodebrg BR001 sejumlah 3,
nah setelah di eksekusi coba buka tabel barang yang tadinya barang
dengan kode BR001 (Rinso) stok: 10, sekarang berkurang menjadi 7.
lakukan test juga pada tabel beli maka stok akan otomatis bertambah…
bagi yang ingin mencoba silahkan download file sql ujicoba tersebut
disini.
Sumber : https://mboloz.wordpress.com/2013/02/22/trigger-mysql-mengurangi-stok/